Virtual Private Cloud (VPC) is a logical isolation of AWS cloud per region where you define the subnets, IP addresses, gateways, and routing. VPC is used to launch AWS resources, and VPC is entirely customizable. You choose CIDR block to be assigned to virtual networks which span across different availability zones, VPC has different components let’s go through them now.
IPv4 VPC CIDR blocks
When you create a VPC, you must specify an IPv4 CIDR block for the VPC. The allowed block size is between a /16 netmask (65,536 IP addresses) and /28 netmask (16 IP addresses)
Planning the IPv4 CIDR Block for a VPC is crucial for scalability; we can add only one additional or secondary CIDR Block to VPC. also, as we will explain in a later stage, we can connect different VPCs in the same or different regions together, as a prerequisite, no overlapping CIDR block can be connected.
Subnets
Subnet can only reside in a single Availability Zone (AZ), Subnets also can be private or public
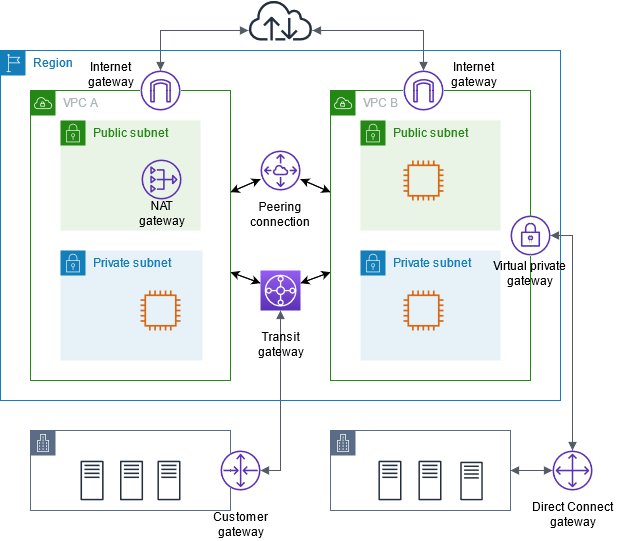
Public Subnet: A public subnet is a subnet that is associated with a route table that has a route to an Internet gateway. This connects the VPC to the Internet and to other AWS services.
Private Subnet: A private subnet is a subnet that is associated with a route table that doesn’t have a route to an internet gateway. Instances in the private subnet are backend servers they don’t accept the traffic from the internet
- Resources in private subnets to connect to the internet using NAT device (NAT Gateway or NAT Instance).
Routing
Routing table is a set of rules that determine where the network traffic is directed, VPC route tables will determine the specific destination that is IP addresses and target where the traffic is needed to be sent.
Gateways and endpoints
Internet Gateways
- An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet. It supports IPv4 and IPv6 traffic.
- An egress-only internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows outbound communication over IPv6 from instances in your VPC to the internet, and prevents the internet from initiating an IPv6 connection with your instances.
VPC Peering
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them privately
- No overlap of CIDR block
- It can be configured between VCPs in the same or different accounts
- Only two peered VPCS can talk to each any other peered VPC or On-prem (VPN) can connect
Transit Gateway
- A transit gateway is (a regional resource) used to connect virtual private clouds (VPC) and on-premises networks, Transit gateway acts as a central hub, routing traffic between VPCs, VPN connections, and AWS Direct Connect connections.
- Eliminate mesh connection created by multiple VPC Peering
- Costly as priced hourly per attachment, data processing, and data transfer.
NAT Devices
- A NAT gateway is a Network Address Translation (NAT) service. You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC but external services cannot initiate a connection with those instances.
- Not recommended You can create your own AMI that provides network address translation and use your AMI to launch an EC2 instance as a NAT instance.
VPC VPN
Connect your VPC to remote networks using AWS Virtual Private Network, one by of four options
- AWS Site-to-Site VPN (IPsec VPN connection between VPC and remote network. Virtual private gateway or transit gateway provides two VPN endpoints (tunnels) for automatic failover)
- AWS Client VPN (AWS Client VPN is a managed client-based VPN service that enables you to securely access your AWS resources or your on-premises network)
- AWS VPN CloudHub (If you have multiple AWS Site-to-Site VPN connections, you can provide secure communication between sites using the AWS VPN CloudHub)
- Third party software VPN appliance from AWS Marketplace
VPC Endpoint
Without Endpoints traffic between VPC and other VPCs or services uses the internet, Using PrivateLink allows the resources in your VPC to connect to services in other VPCs using private IP addresses as if those services were hosted directly in your VPC.
Gateway Endpoints provide reliable connectivity to Amazon S3 and DynamoDB without requiring an internet gateway or a NAT device for your VPC. Gateway endpoints do not enable AWS PrivateLink.
- There is no additional charge for using gateway endpoints.
Interface Endpoints Provide connectivity to anything else that gateway endpoints do
Elastic IP Addresses (EIPs)
AWS maintains a pool of public IP addresses to be assigned to an EC2 Instance. These public IP addresses are called Elastic IP addresses.
Demo

Solutions Architect – Cloud & Infrastructure