With AWS Identity and Access Management (IAM), you can specify who or what can access services and resources in AWS, centrally manage fine-grained permissions, and analyze access to refine permissions across AWS.

https://d1.awsstatic.com/product-marketing/IAM/iam-how-it-works-diagram.04a2c4e4a1e8848155840676fa97ff2146d19012.png
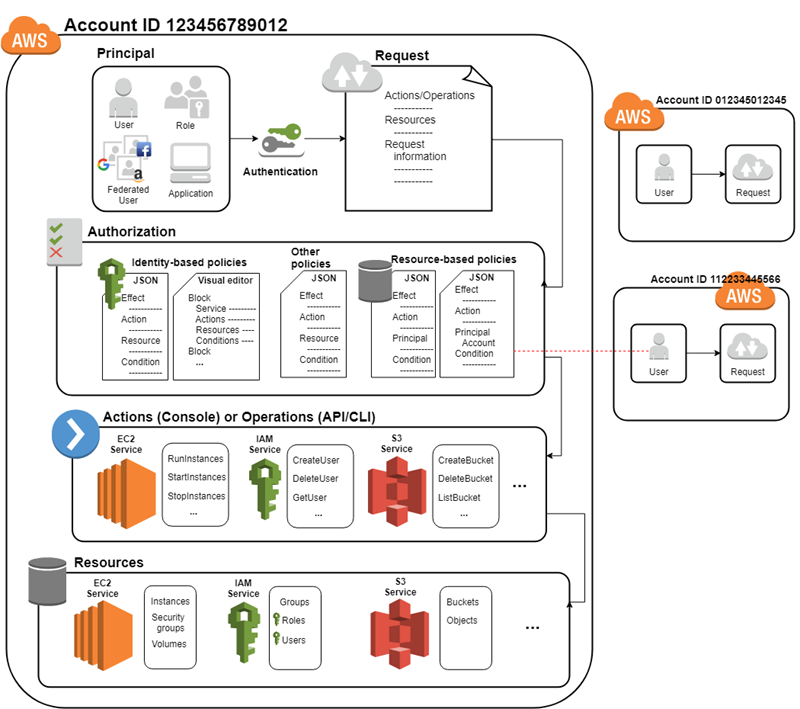
Identity and access management is a key component of any security architecture. AWS IAM Identify user and applies fine-grained permissions and scale with attribute-based access control, also called AAA. The key components of AAA are as follows:
● Authentication: Identifying the Principal can be (User or Role or Federated users or Programmatic access).
● Authorization: Determining if the user is allowed to access the resource by checking AWS IAM Policy
● Accounting: Logging and monitoring the user activities using AWS CloudTrail
https://docs.aws.amazon.com/images/IAM/latest/UserGuide/images/intro-diagram%20_policies_800.png
Principal
A principal is a person or application that can make a request for an action or operation on an AWS resource. The principal is authenticated as the AWS account root user or an IAM entity to make requests to AWS. As a best practice, do not use your root user credentials for your daily work. Instead, create IAM entities (users and roles). You can also support federated users or programmatic access to allow an application to access your AWS account.
Types of principal
Root User
One identity (who created the account) that has complete access to all AWS services and resources in the account.
IAM Users
The person or application that uses it to interact with AWS. A user in AWS consists of a name and credentials (password – Access keys – SSH keys – Server certificates).
By default, a brand new IAM user has no permissions to do anything. The user is not authorized to perform any AWS operations or to access any AWS resources.
Federated users
Users from third-party Identity Providers
IAM Groups
An IAM user group is a collection of IAM users.
IAM Roles
An IAM role is an IAM identity that you can create in your account that has specific permissions. An IAM role is similar to an IAM user, the role is intended to be assumable by anyone. who assumes the role, will be provided with temporary security credentials for your role session.
**IAM role is used by an AWS service to access another service, i.e., EC2 accessing DynamoDB.
IAM Policies
- IAM policy is an AWS object that, when attached to identities (users, groups of users, or roles) or AWS resource will define their permission either allow or deny.
- IAM policies can be either:
- AWS-managed policies are standalone policies created by AWS
- Customer-managed policies are managed by the customer for their account.
- Most policies are stored in AWS as JSON documents.
- AWS supports six types of policies: identity-based policies, resource-based policies, permissions boundaries, Organizations SCPs, ACLs, and session policies. (will focus on two types of policies)
https://docs.aws.amazon.com/images/IAM/latest/UserGuide/images/Types_of_Permissions.diagram.png
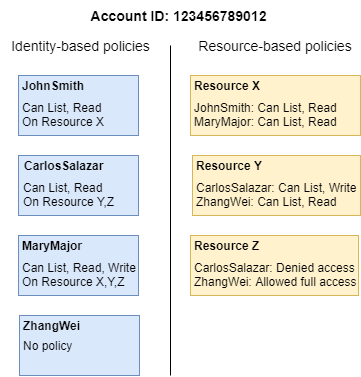
Identity-based policies
- Identity-based policies grant permissions to an identity.
- These policies control what actions an identity (users, groups of users, and roles) can perform, on which resources, and under what conditions.
Resource-based policies
- Resource-based policies grant permissions to the principal that is specified in the policy.
- These policies grant the specified principal permission to perform specific actions on that resource and defines under what conditions this applies.
AWS IAM security best practices
• Use MFA for Users
• Granular access control for the least privileges
• Federate with your existing directory services
• Role-based access and segregation of duties
• Achieve just-in-time access using role assumption
Also, refer to the latest AWS IAM best practices guide

Solutions Architect – Cloud & Infrastructure